Port Forward from Head Office SonicWALL to Host at Remote Branch over Site to Site IPSEC
Requirement
This document has been created to document the configuration
in order to create a port forward through head office to a host at a remote
site connected via IPSEC VPN through the SonicWALL.
The reasoning for not port forwarding direct from the remote
site firewall/router is that the remote site uses a 3G/4G modem to connect to
the internet and therefore does not have its own WAN IP address. By forwarding
the port from the head office over the VPN this overcomes the problem.
Scope
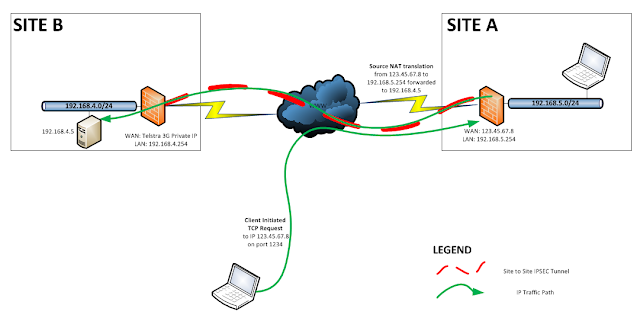
TCP port 1234 needs to be forwarded to host 192.168.4.5 at
remote site B via the WAN IP address 123.45.67.8 at site A. Site A has a static
publicly routable WAN IP address. Site B has a Telstra 3G Private Network that
is not publicly accessible.
NAT Configuration
In order for external (WAN) traffic to pass through the VPN,
the source IP will need to be translated. In order to do this, create a new NAT
rule Under Network -> NAT Policies on the SonicWALL.
Original Source:
ANY
This is set
to ANY so that ANY external WAN IP can access.
Translated
Source: X0 IP
The source
is translated to the IP of the X0 interface which is 192.168.5.254 so it can
transverse the site to site IPSEC VPN tunnel.
Original
Destination: 192.168.4.5
The host at
the remote site (Site B) IP address is 192.168.4.5 – because of the source NAT
translation the traffic will appear to come from 192.168.5.254 over the VPN.
Translated
Destination: Original
No
destination translation is required, so Original is selected.
Original
Service: TCP 1234
TCP 1234 is
the destination port for the desired port forward.
Translated
Service: Original
No service
translation is required, so Original is selected.
Firewall
Configuration
In order for traffic to come in from WAN over the VPN a
WAN->VPN Firewall Policy will need to be added. Under Firewall-> Access
Rules add a new policy from WAN->VPN per below



Comments
Post a Comment